There is a virus that is lurking around the corner. This is one that will have devastating effects on our economy, business, and our personal lives. The virus is nearly undetectable until it has done its damage.
We may not even know that it has spread throughout the country until it’s too late. There is no news because the Internet is down, there is no radio or TV. By that time, the stores are empty, there is no gas at the filling stations, no electricity in your home, and you are in a panic.
What is this horrible virus that has shut down everything? It’s not a living organism – it’s a computer virus that was unleashed by a massive cyber-attack on our infrastructure.
Do you think that could never happen? Ask yourself – did you think we could ever be hit with a viral pandemic that would effectively shut down the entire country for months on end? Would you have imagined that we’d still be wearing masks everywhere, including in schools? I’m not saying that COVID-19 was intentional, but bio-virus attacks have been predicted for years. Regardless of the source or motive, the result is the same. America and countries worldwide have been brought to their knees. And it is still happening right now …
The other kind of virus is the computer virus. We have been doing battle with this one for many years now, and the onslaught of attacks is relentless. Think you are protected? Think again. Here are a few of the cyber-attacks just in the past year – so far:
SOURCE: Center for Strategic and International Studies
August 2021. A cyberattack on the government of Belarus has compromised dozens of police and interior ministry databases.
August 2021. A hacking group targeted a high-profile Iranian prison, uncovering documents, videos, and images that displayed the violent treatment of its prisoners.
August 2021. A cyber-espionage group linked to one of Russia’s intelligence forces targeted the Slovak government from February to July 2021 through spear-fishing attempts.
August 2021. Russia targeted and blocked content on “smart voting” app created by Kremlin critic Alexei Navalny and his allies intended to organize voting against the Kremlin in next month’s parliamentary elections.
August 2021. T-Mobile suffered a data breach that led the hacker to access the personal details of over 50 million people. The hacker stated he discovered an unprotected router exposed on the internet allowing him access to the network.
August 2021. Hacks initially attributed to Iran in 2019 and 2020 were found to be conducted by Chinese operatives. The cyberattack broke into computers across Israel’s government and tech companies.
August 2021. In one of the largest cryptocurrency heists, a hacker stole around $600 million from Blockchain site Poly Network. The hacker then returned $340 million directly and transferred $268 million to a digital wallet jointly controlled by them and Poly Network. However, the funds in the wallet remain inaccessible until the hacker provides the digital key.
August 2021. A cyberattack on the Covid-19 vaccine-scheduling website for the Italian region of Lazio forced the website to temporarily shut down. New vaccination appointments were unable to be scheduled for several days after the attack.
August 2021. Various Chinese cyber-espionage groups are responsible for the hacks of at least five major Southeast Asian telecommunication providers beginning in 2017. The attacks were carried out by three different hacking groups and are seemingly unlinked despite all groups having a connection to Chinese espionage efforts.
July 2021. A data leak impacted Northern Ireland’s COVIDCert online vaccination certification service, causing their Department of Health to temporarily suspend the portal.
July 2021. Estonia stated a Tallinn-based hacker downloaded 286,438 ID photos from government database, exposing a vulnerability in a platform managed by their Information System Authority (RIA).
July 2021. A widespread APT operation was discovered against users in Southeast Asia, believed to be spearheaded by Chinese entities. Researchers found a total of 100 victims in Myanmar and 1,400 in the Philippines, including many government entities.
July 2021. The Japan 2020 Olympics was subject to data breach exposing the personal credentials of volunteers and ticket holders. The information included usernames, passwords, addresses, and bank account numbers.
July 2021. The United States, the European Union, NATO and other world powers released joint statements condemning the Chinese government for a series of malicious cyber activities. They attributed responsibility to China for the Microsoft Exchange hack from early 2021 and the compromise of more than 100,000 servers worldwide.
July 2021. Transnet Port Terminals (TPT), South Africa’s state-run ports operator and freight rail monopoly, had its rail services disrupted after a hack by unknown actors. Transnet reportedly declared it an act “force majeure.”
July 2021. Several countries used Pegasus, surveillance software created by NSO Group that targets iPhone and Android operating systems, on devices belonging to activists, politicians, and journalists.
July 2021. The FBI and the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a statement exposing a spearfishing campaign by Chinese state-sponsored hackers between 2011 and 2013. The campaign targeted oil and natural gas pipeline companies in the United States.
July 2021. Iran used Facebook accounts to pose as recruiters, journalists, and NGO affiliates, targeting U.S. military personnel. The hackers sent malware-infected files or tricked targets into submitting sensitive credentials to phishing sites.
July 2021. The Russian defense ministry claimed it was hit with a DDoS attack that caused its website to shut down, stating the attack came from outside the Russian Federation.
July 2021. Norway attributed a March 2021 cyberattack on parliament’s e-mail system to China.
July 2021. Iran’s transport and urbanization ministry was the victim of a cyber-attack that impacted display boards at stations throughout the country. The attack caused delays and cancellations of hundreds of trains across Iran.
July 2021. Russian hackers exploited a vulnerability in Kaseya’s virtual systems/server administrator (VSA) software allowing them to deploy a ransomware attack on the network. The hack affected around 1,500 small and midsized businesses, with attackers asking for $70 million in payment.
July 2021. The Ukranian Ministry of Defense claimed its naval forces’ website was targeted by Russian hackers who published fake reports about the international Sea Breeze-2021 military drills.
June 2021. Russia claimed that Vladimir Putin’s annual phone-in session was targeted by DDoS attacks.
June 2021. A Chinese-speaking hacking group spearheaded an ongoing espionage effort against the Afghan government through phishing emails. Hackers posed as the Office of the President of Afghanistan and targeted the Afghan National Security Council (NSC).
June 2021. The Iranian government launched a wide scale disinformation campaign, targeting WhatsApp groups, Telegram channels and messaging apps used by Israeli activists. The campaign aimed to advance political unrest and distrust in Israel.
June 2021. Chinese actors targeted organizations, including Verizon and the Metropolitan Water District of Southern California using a platform used by numerous government agencies and companies for secure remote access to their networks.
June 2021. Hackers linked to Russia’s Foreign Intelligence Service installed malicious software on a Microsoft system that allowed hackers to gain access to accounts and contact information.
June 2021. The U.S. and British governments announced the Russian General Staff Main Intelligence Directorate (GRU) used a series of brute force access attempts against hundreds of governments and private sector targets worldwide from 2019 to 2021, targeting organizations using Microsoft Office 365® cloud services.
June 2021. United States Naval Institute (USNI) claimed the tracking data of two NATO ships, the U.K. Royal Navy’s HMS Defender and the Royal Netherlands Navy’s HNLMS Evertsen, was falsified off the coast of a Russian controlled naval base in the Black Sea. The faked data positioned the two warships at the entrance of a major Russian naval base.
June 2021. A cyberattack reportedly from Russia targeted more than 30 prominent Polish officials, ministers and deputies of political parties, and some journalists by compromising their email inboxes.
June 2021. Sol Oriens, a small government contractor that works for the Department of Energy on nuclear weapons issues, was attacked by the Russia-linked hacking group REvil.
June 2021. A spreadsheet was leaked containing classified personal details of the 1,182 United Kingdom’s Special Forces soldiers on WhatsApp.
June 2021. A ransomware attack targeted iConstituent, a newsletter service used by U.S. lawmakers to contact constituents.
June 2021. Hackers working on behalf of Russian intelligence services are believed to have hacked Netherlands police internal network in 2017. The attack occurred during the country’s investigation of the Malaysia Airlines Flight 17 (MH17) that was shot down in 2014.
May 2021. LineStar Integrity Services, a pipeline-focused business, was hit by a ransomware attack the same time as the Colonial Pipeline, with 70 gigabytes of its internal files being stolen.
May 2021. A North Korean cyberattack on South Korea’s state-run Korea Atomic Energy Research Institute (KAERI) occurred through a vulnerability in a vendor’s VPN.
May 2021. The world’s largest meat processing company, Brazilian-based JBS, was the victim of a ransomware attack. The attack shut down facilities in the United States, Canada and Australia. The attack was attributed to the Russian speaking cybercrime group, REvil.
May 2021. On May 24th, hackers gained access to Fujitsu’s systems and stole files belonging to multiple Japanese government entities. So far four government agencies have been impacted.
May 2021. Cybersecurity researchers identified a North Korean hacking group to be responsible for a cyber espionage campaign, targeting high profile South Korean government officials, utilizing a phishing methodology. The group’s targets were based in South Korea and included: the Korea Internet and Security Agency (KISA), ROK Ministry of Foreign Affairs, Ambassador of the Embassy of Sri Lanka to the State (in ROK), International Atomic Energy Agency Nuclear Security Officer, Deputy Consul General at Korean Consulate General in Hong Kong, Seoul National University, and Daishin Securities.
May 2021. On May 14, Ireland’s national health service, the Health Service Executive (HSE), was the victim of a ransomware attack. Upon discovering the attack, government authorities shut down the HSE system. The attackers utilized the Conti ransomware-as-a-service (RaaS), which is reported to be operated by a Russia-based cybercrime group.
May 2021. The FBI and the Australian Cyber Security Centre warned of an ongoing Avaddon ransomware campaign targeting multiple sectors in various countries. The reported targeted countries are Australia, Belgium, Brazil, Canada, China, Costa Rica, Czech Republic, France, Germany, India, Indonesia, Italy, Jordan, Peru, Poland, Portugal, Spain, UAE, UK, US. The targeted industries include: academia, airlines, construction, energy, equipment, financial, freight, government, health, it, law enforcement, manufacturing, marketing, retail, pharmaceutical.
May 2021. On May 6, the Colonial Pipeline, the largest fuel pipeline in the United States, was the target of a ransomware attack. The energy company shut down the pipeline and later paid a $5 million ransom. The attack is attributed to DarkSide, a Russian speaking hacking group.
May 2021. On May 4th and 5th, the Norwegian energy technology company Volue was the victim of a ransomware attack. The attack resulted in the shutdown of water and water treatment facilities in 200 municipalities, affecting approximately 85% of the Norwegian population.
May 2021. A large DDoS attack disabled the ISP used by Belgium’s government, impacting more than 200 organizations causing the cancellation of multiple Parliamentary meetings
May 2021. A Chinese hacking group compromised a Russian defense contractor involved in designing nuclear submarines for the Russian navy.
April 2021. A hacking group compromised the social media accounts of Polish officials and used them to disseminate narratives critical of NATO. German authorities have reported that the same group has also attempted to compromise members of the Bundestag and state parliament.
April 2021. Hackers linked to the Chinese military conducted an espionage campaign targeting military and government organizations in Southeast Asia beginning in 2019
April 2021. Malware triggered an outage for airline reservation systems that caused the networks of 20 low-cost airlines around the world to crash
April 2021. Russian hackers targeted Ukrainian government officials with spear phishing attempts as tensions between the two nations rose during early 2021.
April 2021. Hackers linked to Palestinian intelligence conducted a cyber espionage campaign compromising approximately 800 Palestinian reporters, activists, and dissidents both in Palestine and more broadly across the Middle East.
April 2021. Two state-backed hacking groups—one of which works on behalf of the Chinese government—exploited vulnerabilities in a VPN service to target organizations across the U.S. and Europe with a particular focus on U.S. defense contractors.
April 2021. MI5 warned that over 10,000 UK professional shave been targeted by hostile states over the past five years as part of spear phishing and social engineering campaigns on LinkedIn.
April 2021. Swedish officials disclosed that the Swedish Sports Confederation was hacked by Russian military intelligence in late 2017 and early 2018 in response to accusations of Russian government-sponsored doping of Russian athletes.
April 2021. New York City’s Metropolitan Transportation Authority (MTA) was hacked by Chinese-backed actors but were unable to gain access to user data or information systems.
April 2021. French security researchers found that the number of attacks hitting critical French businesses increased fourfold in 2020 during the COVID-19 pandemic.
April 2021. The European Commission announced that the EC and multiple other EU organizations were hit by a major cyberattack by unknown.
April 2021. Chinese hackers launched a months-long cyber espionage campaign during the second half of 2020 targeting government agencies in Vietnam with the intent of gathering political intelligence
March 2021. The North Korean hacking group responsible for a set of attacks on cybersecurity researchers in January 2021 launched a new campaign targeting infosec professionals using fake social media profiles and a fake website for a non-existent security service company target.
March 2021. Suspected Iranian hackers targeted medical researchers in Israel and the U.S. in an attempt to steal the credentials of geneticists, neurologists, and oncologists in the two countries
March 2021. Suspected Russian hackers stole thousands of emails after breaching the email server of the U.S. State Department
March 2021. Suspected state hackers targeted the Australian media company Nine Entertainment with a ransomware variant, disrupting live broadcasts and print production systems.
March 2021. Suspected Russian hackers attempted to gain access to the personal email accounts of German parliamentarians in the run-up to Germany’s national elections
March 2021. U.S. Cyber Command confirmed that it was assisting Columbia in responding to election interference and influence operations.
March 2021. The head of U.S. Cyber Command testified that the organization had conducted more than two dozen operations to confront foreign threats ahead of the 2020 U.S. elections, including eleven forward hunt operations in nine different countries.
March 2021. A group of Chinese hackers used Facebook to send malicious links to Uyghur activists, journalists, and dissidents located abroad.
March 2021. The Indian Computer Emergency Response Team found evidence of Chinese hackers conducting a cyber espionage campaign against the Indian transportation sector
March 2021. Polish security services announced that suspected Russian hackers briefly took over the websites of Poland’s National Atomic Energy Agency and Health Ministry to spread false alerts of a nonexistent radioactive threat.
March 2021. Both Russian and Chinese intelligence services targeted the European Medicines Agency in 2020 in unrelated campaigns, stealing documents relating to COVID-19 vaccines and medicines.
March 2021. Ukraine’s State Security Service announced it had prevented a large-scale attack by Russian FSB hackers attempting to gain access to classified government data.
March 2021. Lithuania’s State Security Department declared that Russian hackers had targeted top Lithuanian officials in 2020 and used the country’s IT infrastructure to carry out attacks against organizations involved in developing a COVID-19 vaccine.
March 2021. Suspected Iranian hackers targeted government agencies, academia, and the tourism industry in Azerbaijan, Bahrain, Israel, Saudi Arabia, and the UAE as part of a cyber espionage campaign.
March 2021. Chinese government hackers targeted Microsoft’s enterprise email software to steal data from over 30,000 organizations around the world, including government agencies, legislative bodies, law firms, defense contractors, infectious disease researchers, and policy think tanks.
March 2021. Suspected Chinese hackers targeted electricity grid operators in India in an apparent attempt to lay the groundwork for possible future attacks.
February 2021. A Portuguese-speaking cybercriminal group accessed computer systems at a division of Oxford University researching COVID-19 vaccines, and are suspected to be selling the data they collected to nation states.
February 2021. North Korean hackers targeted defense firms in more than a dozen countries in an espionage campaign starting in early 2020.
February 2021. Hackers associated with the Chinese military conducted a surveillance campaign against Tibetans both in China and abroad.
February 2021. Russian hackers compromised a Ukrainian government file-sharing system and attempted to disseminate malicious documents that would install malware on computers that downloaded the planted files.
February 2021. Hackers linked to the Vietnamese government conducted a nearly three-year cyber espionage campaign against human rights advocates in the country by using spyware to infiltrate individuals’ systems, spy on their activity, and exfiltrate data.
February 2021. Ukrainian officials reported that a multi-day distributed denial-of-service attack against the website of the Security Service of Ukraine was part of Russia’s hybrid warfare operations in the country.
February 2021. The US Department of Justice indicted three North Korean hackers for conspiring to steal and extort more than $1.3 billion in cash and cryptocurrencies.
February 2021. Iranian hackers took control of a server in Amsterdam and used it as a command and control center for attacks against political opponents in the Netherlands, Germany, Sweden, and India.
February 2021. North Korean hackers attempted to break into the computer systems of pharmaceutical company Pfizer to gain information about vaccines and treatments for the COVID-19.
February 2021. Suspected Iranian hackers targeted government agencies in the UAE as part of a cyber espionage campaign related to the normalizations of relations with Israel.
February 2021. The French national cybersecurity agency announced that a four-year campaign against French IT providers was the work of a Russian hacking group.
February 2021. Suspected Indian hackers targeted over 150 individuals in Pakistan, Kazakhstan, and India using mobile malware, including those with links to the Pakistan Atomic Energy Commission, the Pakistan Air Force, and election officials in Kashmir.
February 2021. Ten members of a cybercriminal gang were arrested after a campaign where they tricked telecom companies into assigning celebrities’ phone numbers to new devices, stealing more than $100 million worth of cryptocurrencies.
February 2021. Unknown hackers attempted to raise levels of sodium hydroxide in the water supply of Oldsmar, Florida by a factor of 100 by exploiting a remote access system.
February 2021. Two Iranian hacking groups conducted espionage campaigns against Iranian dissidents in sixteen countries in the Middle East, Europe, South Asia, and North America.
January 2021. Hackers linked to Hezbollah breached telecom companies, internet service providers, and hosting providers in the US, UK, Egypt, Israel, Lebanon, Jordan, Saudi Arabia, the UAE, and the Palestinian Authority for intelligence gathering and data theft.
January 2021. North Korean government hackers engaged in a sophisticated social engineering campaign against cybersecurity researchers that used multiple fake twitter accounts and a fake blog to drive targets to infected sites or induce them to open infected attachments in emails asking the target to collaborate on a research project.
January 2021. Suspected Indian hackers active since 2012 were attacked business and governments across South and East Asia, with a particular emphasis on military and government organizations in Pakistan, China, Nepal, and Afghanistan, and businesses involved in defense technology, scientific research, finance, energy, and mining.
January 2021. Unidentified hackers breached one of the data centers of New Zealand’s central bank.
January 2021. Hackers linked to the Chinese government were responsible for ransomware attacks against five major gaming and gambling countries, demanding over $100 million in ransom.
And these don’t even include standard businesses. Those attacks number in the tens of thousands! Here are a few:
- Buffalo Public Schools
- Acer Computers
- CNA Financial
- Applus Technologies
- Quanta Computer
- ExaGrid
- Colonial Pipeline
- JBS USA
- US State Department
- SolarWinds
- Yahoo
- Mariott
- Adobe
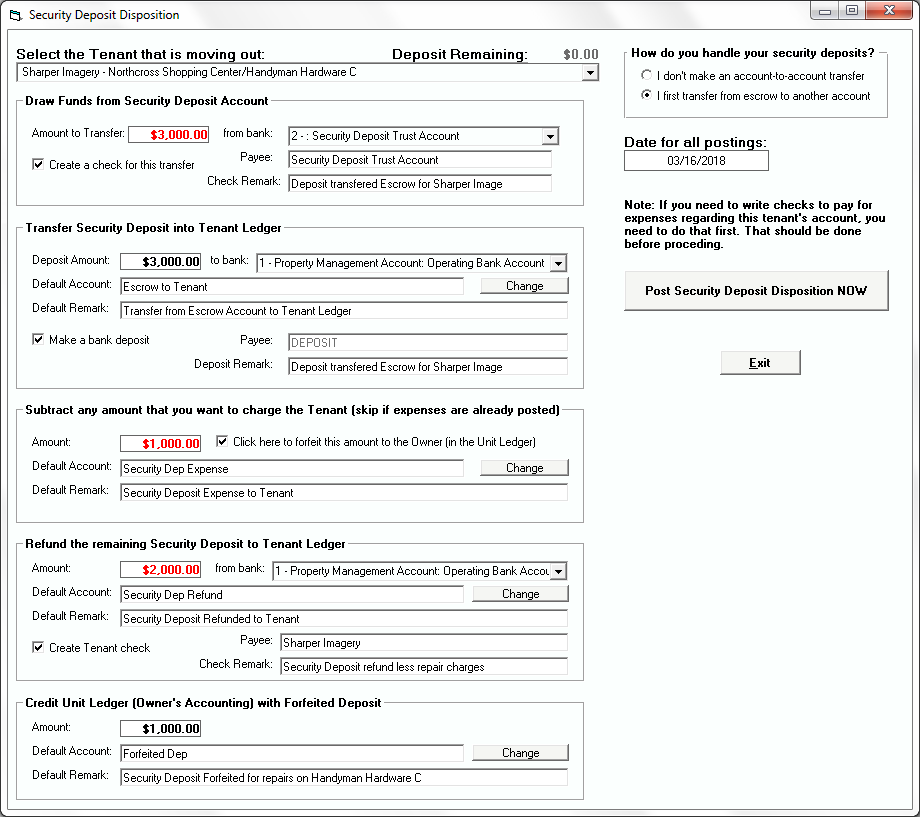
- Midwest Property Management
- Wolfe and Associates Property Management
“Due to lack of federal oversight and regulation, property management companies’ cybersecurity programs may be relatively less developed and less sophisticated than in other industries. This could make them a more attractive target for cybercriminals looking for an easy way to steal personal data. We hear a lot in the news about data being exposed or stolen by cyberattacks in healthcare, banking and retail industries. But we tend to hear less about such attacks in the property management industry, even though they have happened before and will likely happen again. As a result, the risk of cyberattacks in the property management industry may be overlooked and underestimated.” Source: Ellen Clark, Rental Housing Journal
“The real estate industry accounts for a large number of financial transactions that involve sensitive information. This information tends to include bank account numbers and the buyer’s personal data based on the real estate system stored via the cloud. With a large amount of sensitive data on the cloud, hackers are finding real estate data is more accessible than ever before. “ Source: Zev Brodsky, Perimeter 81
If you have cloud or web-based software, just be careful to have data backups, redundant servers, and choose your property management software carefully. You still need to protect your local computers in addition to the online software.
If you have desktop-based software, be sure that your Internet routers have built-in security, and that you have virus and other protection on each of your computers. Make local backups on a regular basis and consider online backups as well.
Author, Wayne Gathright, W G Software, Inc.
Developers of Tenant File Property Management Software

 We thought that the coronavirus would be a blip in the rear-view mirror by now, but it is more like an annoying car that won’t pass you but rides your bumper. Every one of us had found ways to deal with it, but many of us have had to deal with sickness, heartache, and fear of the unknown.
We thought that the coronavirus would be a blip in the rear-view mirror by now, but it is more like an annoying car that won’t pass you but rides your bumper. Every one of us had found ways to deal with it, but many of us have had to deal with sickness, heartache, and fear of the unknown.




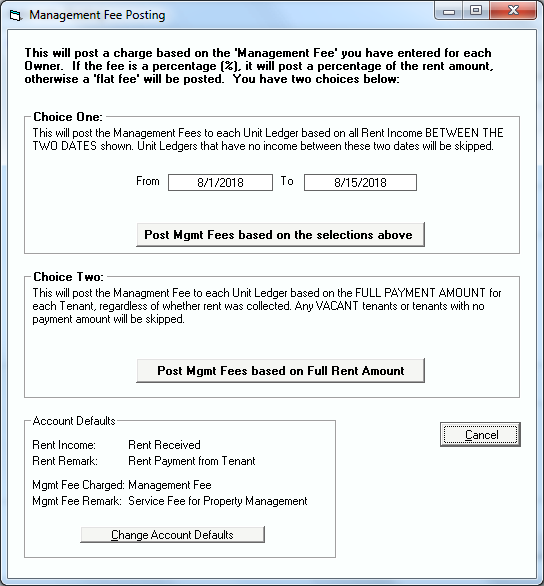
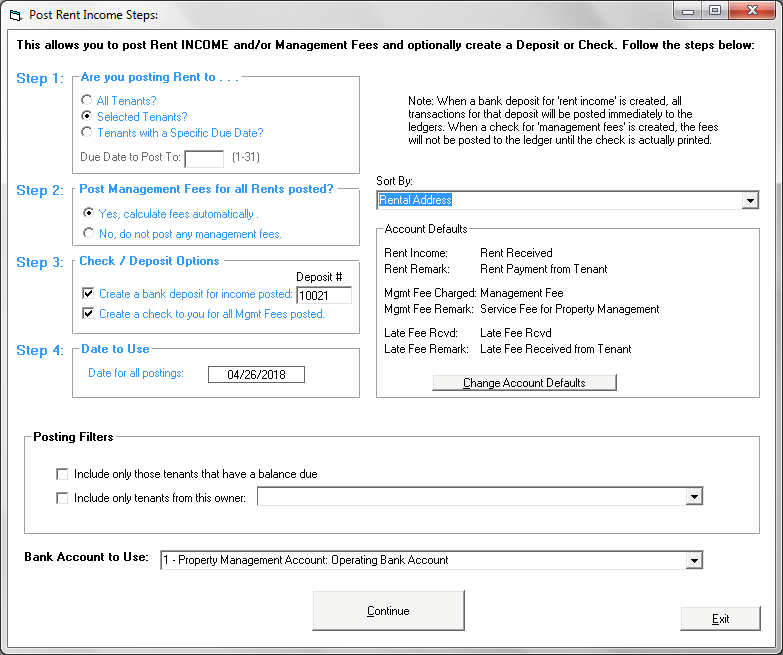 Step 1:
Step 1: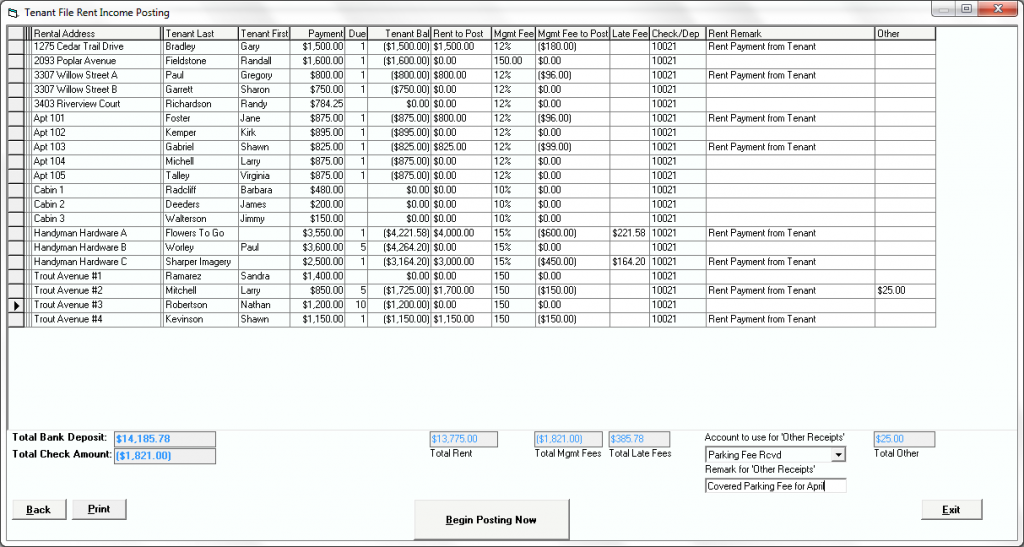 Enter the correct rental income amount received for each Tenant in the ‘Rent To Post’ column if you previously entered ‘Selected Tenants’ in Step 1. If you entered ‘All Tenants’ under Step 1, the monthly payment amount for each tenant will be completed for you in this column. Only the ‘white’ columns, such as the ‘Rent to Post’, ‘Mgmt Fee to Post’, ‘Late Fee’ Received, ‘Remark’ and the ‘Other’ column can be edited. Once you have entered the amounts from your rent checks and clicked down to the next line, the ‘Total Rent’ field will calculate and will be the total of all of your postings. This will be the amount of the deposit created, if you choose to create a deposit. It is very important that you make sure that this total balances to your checks in hand.
Enter the correct rental income amount received for each Tenant in the ‘Rent To Post’ column if you previously entered ‘Selected Tenants’ in Step 1. If you entered ‘All Tenants’ under Step 1, the monthly payment amount for each tenant will be completed for you in this column. Only the ‘white’ columns, such as the ‘Rent to Post’, ‘Mgmt Fee to Post’, ‘Late Fee’ Received, ‘Remark’ and the ‘Other’ column can be edited. Once you have entered the amounts from your rent checks and clicked down to the next line, the ‘Total Rent’ field will calculate and will be the total of all of your postings. This will be the amount of the deposit created, if you choose to create a deposit. It is very important that you make sure that this total balances to your checks in hand.